A content-centered experience is something closely connected to gesture-based navigation. It serves a purpose of removing unnecessary design clutter and keeping the user focused on the app content, and it also serves an aesthetic role. The less buttons, the better – usually.
Let’s put it this way: if you end up on a website or within an app, you usually went there with a clear purpose. You want to gather information, learn or experience something. You don’t want anything unnecessary. Therefore, the aim of a content-centered experience is to use your phone’s screen as much as possible.
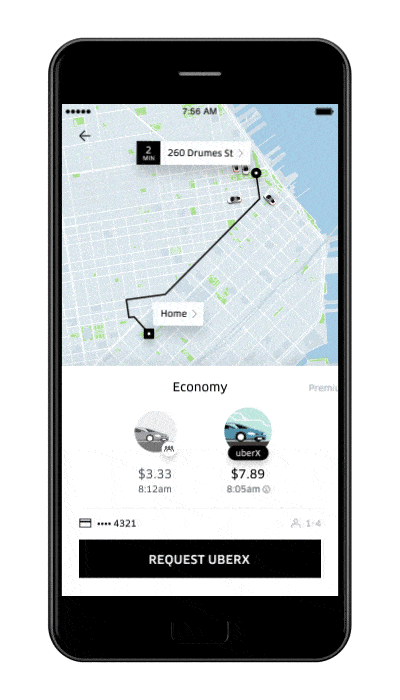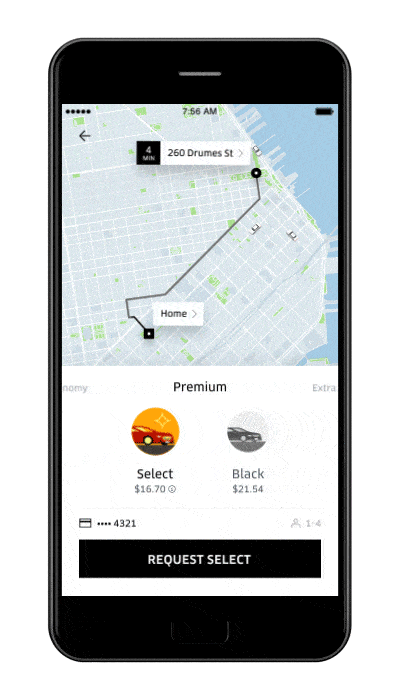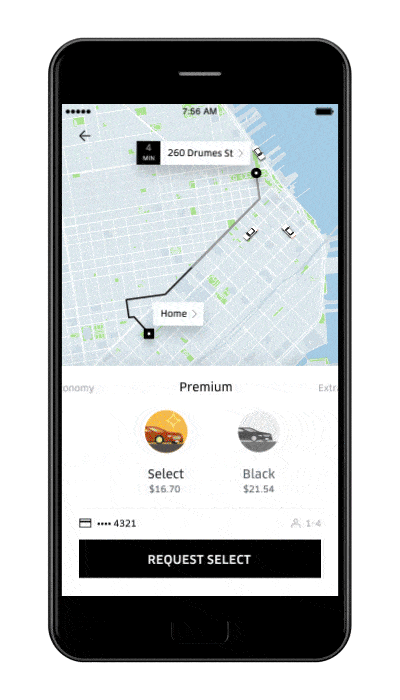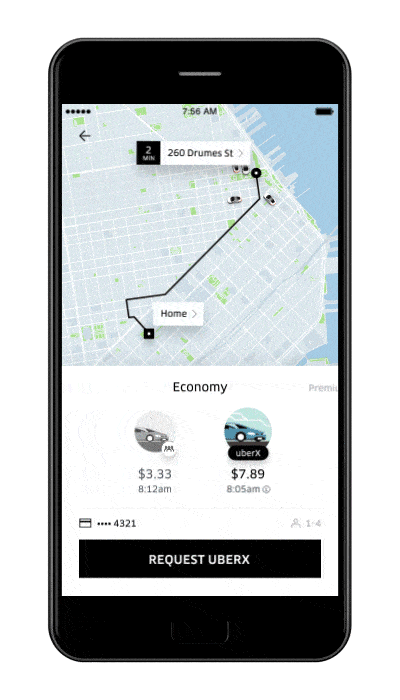
Full-Screen Experiences (with Galaxy S8 and iPhone X on the Market)
Since the launch of the Samsung Galaxy S8, iPhone X, or even OnePlus 5T, the debate on full-screen app experiences is a no-brainer.
You just have to take it into consideration. There’s simply no other option.
When manufacturers decide to deliver a smartphone with a bezel-less screen, why not use it to create more immersive experiences for your users?
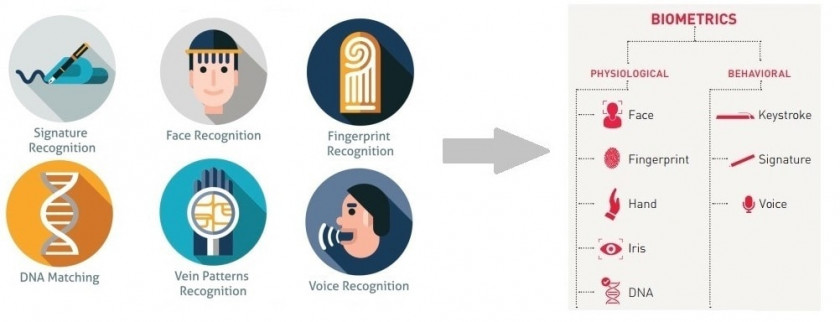
Biometrics
Biometrics in smartphones are not just fingerprint scanners. First introduced in 2013 with the iPhone 5S, fingerprint security is now being replaced by Face ID and similar solutions like Intel RealSense Camera.
In 2018, passwords will remain widely used due to their universalness. Everybody can use them. Biometrics is simply more convenient, although it requires a more complicated and costly device.
Before we continue with what biometrics might evolve to, let’s explain two terms closely associated with the topic. I’ll quote Gemalto experts on that.
“Biometric authentication is the process of comparing data for the person’s characteristics to that person’s biometric “template” in order to determine resemblance. The reference model is the first store in a database or a secure portable element like a smart card. The data stored is then compared to the person’s biometric data to be authenticated. Here it is the person’s identity which is being verified.”
“Biometric identification consists of determining the identity of a person. The aim is to capture an item of biometric data from this person. It can be a photo of their face, a record of their voice, or an image of their fingerprint. This data is then compared to the biometric data of several other persons kept in a database.”